
TL;DR Link to heading
An issue in Microsoft Teams Web allows for the bypass of the “External” label in incoming call boxes when contacting an external domain user directly via call without prior messaging, potentially leading to security risks (vishing).
Overview Link to heading
While conducting Red Teaming activities I found an issue on Microsoft Teams, a “low” rated security feature bypass according to MSRC (Microsoft Security Response Center). Despite its classification, I believe it’s a good point for Red Teamers as well as Customers, as it can greatly influence outcomes of the Red Team.
MS Teams Behavior for External Calls Link to heading
MS Teams calls from external users display the “External” label to indicate their origin. This label serves as a defense-in-depth mitigation to help users identify potentially risky calls. However, the vulnerability discovered allows for this label to be bypassed, potentially leading to misrepresentation of call origin and potential security risks.
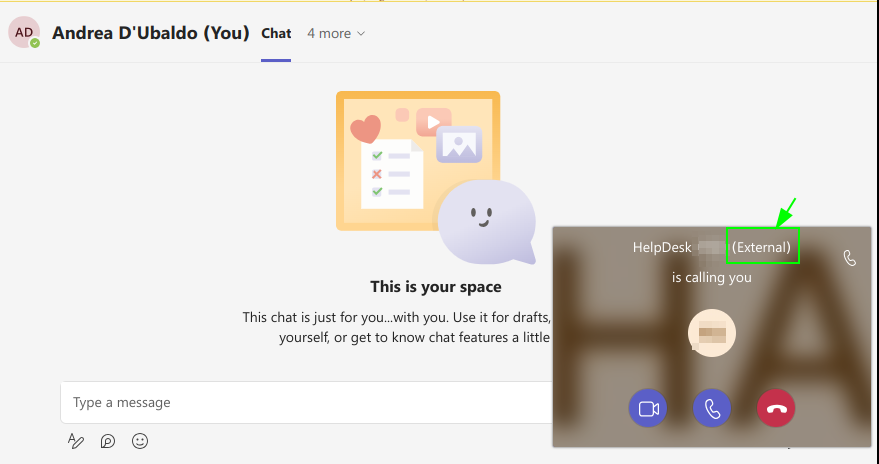
Bypass of the “External” Label Link to heading
The vulnerability in question allows for a bypass of the “External” label in incoming call boxes when contacting an external domain user directly via call without prior messaging. This means that when initiating a call to an external domain user on MS Teams Web without sending any prior message, the usual indication of “External” in the incoming call box is bypassed.
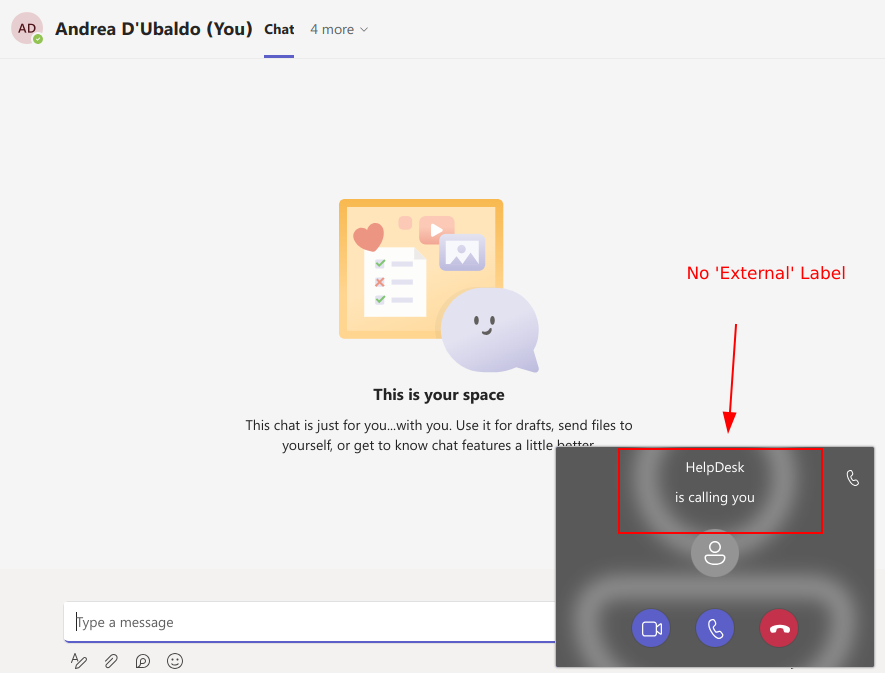
Users could potentially be misled into thinking that the call is internal, thereby compromising security protocols regarding external communications. This could lead to users unwittingly disclosing sensitive information or engaging in unauthorized communications.
It’s important to note that this vulnerability is specific to MS Teams Web, and it’s not a systemic issue across all platforms.
Disclosure Timeline Link to heading
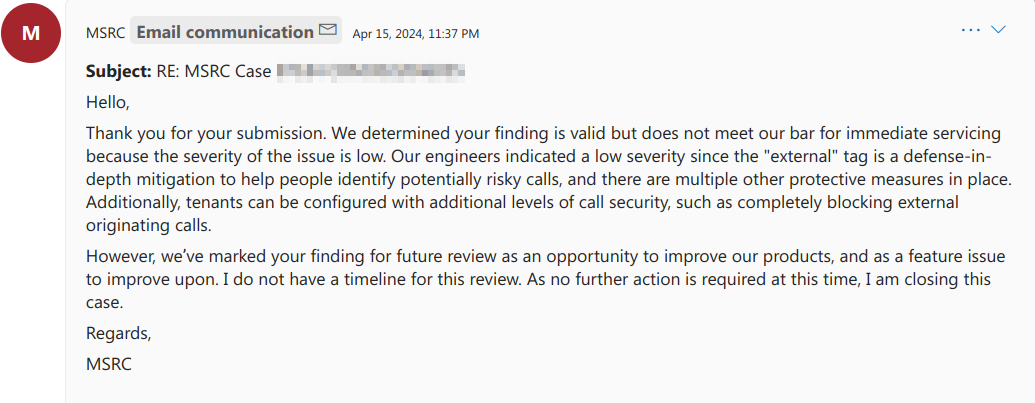
I discovered the vulnerability on April 12, 2024, and was reported to Microsoft on the same day. Microsoft acknowledged the finding but determined that it does not meet their bar for immediate servicing due to the low severity of the issue. However, they have marked the finding for future review as an opportunity to improve their products and as a feature issue to enhance upon.
Mitigation Link to heading
To mitigate the risks associated with this vulnerability, there are two different approaches that organizations can consider:
- Restrict External Domains: block or restrict external domains in MS Teams, which would prevent users from receiving calls from external domains. This is a more restrictive approach, but it can help reduce the risk of calls from external domains.
- Security Awareness Training: provide security awareness training to employees, not just for common phishing campaigns but also for variants like messaging apps phishing and vishing. This can help employees identify and avoid potentially risky calls, even if the “External” label is bypassed.