
Exploiting OAuth Device Login for Phishing and Abusing Microsoft Graph API with AADInternals Link to heading
TL;DR Link to heading
Device Code Phishing is a technique that allows attackers to bypass traditional credential-based phishing defenses by exploiting legitimate OAuth authentication mechanisms. By tricking users into entering a device code on Microsoft’s official login page, attackers can gain access to Microsoft 365 accounts and abuse Microsoft Graph API to read messages, emails, send phishing messages, and extract sensitive data. This article explains how the attack works and provides mitigation strategies to prevent exploitation.
OAuth-Based Phishing Link to heading
In February 2025, Microsoft publicly disclosed the discovery of a phishing campaign that exploited the OAuth 2.0 Device Authorization Flow to gain unauthorized access to Microsoft 365 accounts. While the technique itself is not new, its execution in this campaign demonstrates the increasing refinement of device code phishing, a deceptive tactic that enables cybercriminals to sidestep traditional anti-phishing defenses with striking effectiveness.
This type of attack takes advantage of legitimate authentication processes, tricking users into unknowingly granting OAuth permissions to adversary-controlled applications as well as legitimate Microsoft applications. Once access is granted, attackers can utilize Microsoft Graph API to impersonate the victim, extracting sensitive data, spreading internal phishing emails, and moving laterally across an organization’s cloud environment.
In this article, I provide a step-by-step breakdown of how this attack works, explaining the key principles of OAuth device code phishing, the tools and methods adversaries leverage, such as AADInternals, and the countermeasures organizations should adopt to mitigate these security risks.
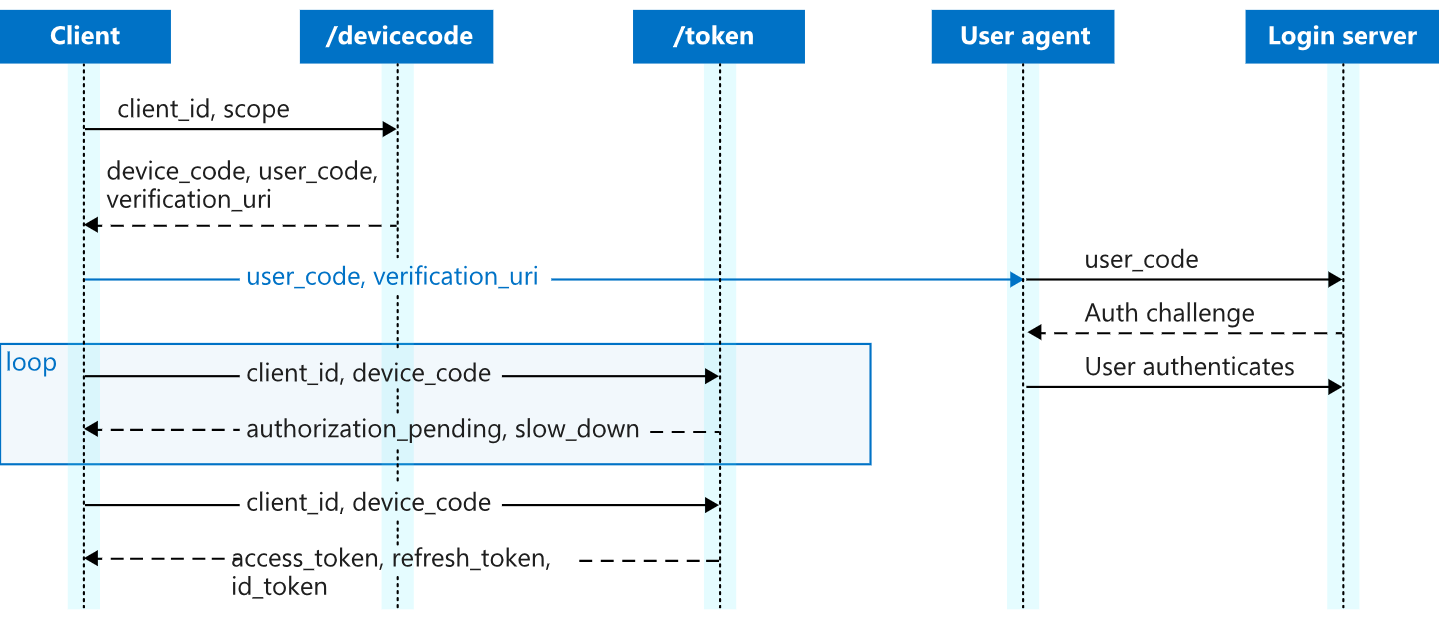
Understanding the OAuth Device Code Flow Link to heading
OAuth 2.0 provides various authentication flows designed for different scenarios. The device code flow is specifically intended for devices that lack conventional input interfaces, such as IoT devices, smart TVs, and command-line authentication mechanisms in cloud environments. Instead of entering credentials directly on the requesting device, users authenticate via a separate browser session, improving usability but simultaneously creating a potential attack surface.
OAuth Device Login Attack Link to heading
Adversaries exploit this process by socially engineering victims into authorizing OAuth applications or even legitimate Microsoft applications using public client IDs through Microsoft’s legitimate authentication system.
1. Attacker Requests a Device Code Link to heading
The attacker initiates the device code flow by sending a request to Microsoft’s OAuth endpoint:
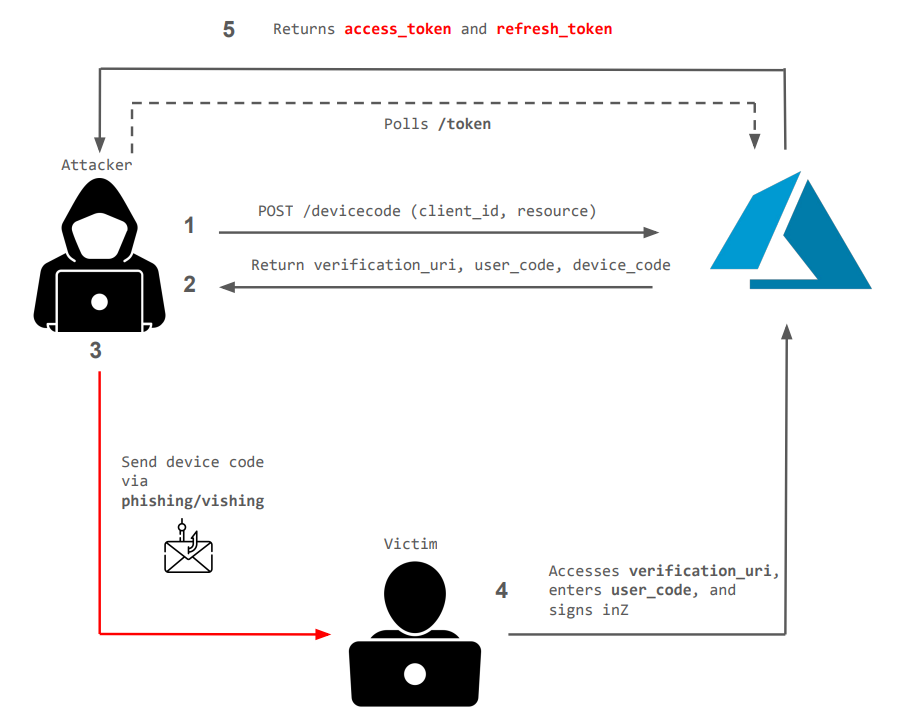
POST https://login.microsoftonline.com/common/oauth2/devicecode
Content-Type: application/x-www-form-urlencoded
client_id=<attacker_application_id>&scope=User.Read
Microsoft responds with a device_code, user_code, and a verification_uri, instructing the user to complete authentication.
2. Victim Authentication Process Link to heading
The victim receives a deceptive message, often via email, chat, or another social engineering vector, directing them to https://microsoft.com/devicelogin to enter a user code.
Because this process occurs on Microsoft’s official website, security tools fail to flag it as suspicious.
The victim unknowingly grants OAuth access to an attacker-controlled application.
3. Attacker Retrieves an OAuth Access Token Link to heading
Once the victim authenticates, the attacker continuously polls Microsoft’s OAuth token endpoint, sending requests with the obtained device_code until the victim completes authentication. When authentication is confirmed, Microsoft issues an access_token, which the attacker retrieves and uses to interact with Microsoft Graph API on behalf of the victim.
POST https://login.microsoftonline.com/common/oauth2/token
Content-Type: application/x-www-form-urlencoded
client_id=<attacker_application_id>&grant_type=urn:ietf:params:oauth:grant-type:device_code&device_code=<device_code>
The attacker now possesses an access_token, allowing unrestricted interaction with Microsoft Graph API using the victim’s privileges.
How Attackers Exploit Microsoft Graph API Link to heading
With a valid OAuth token in hand, adversaries can interact with Microsoft Graph API, carrying out a range of malicious operations such as:
- Extracting Emails:
GET https://graph.microsoft.com/v1.0/me/messages - Sending Internal Phishing Emails:
POST https://graph.microsoft.com/v1.0/me/sendMail - Accessing OneDrive and SharePoint Files:
GET https://graph.microsoft.com/v1.0/me/drive/root/children - Altering Calendar Events for Social Engineering Purposes:
PATCH https://graph.microsoft.com/v1.0/me/events/{id}
This approach enables attackers to conduct stealthy, internal phishing attacks, persist within cloud environments, and escalate privileges undetected.
AADInternals and GraphRunner Link to heading
AADInternals is an advanced toolkit primarily designed for penetration testing and security research within Azure AD environments. While invaluable for ethical hacking purposes, both AADInternals and GraphRunner can be used by malicious actors to:
- Extract OAuth Tokens for Unauthorized API Access
- Obtain Tenant information
- Dump Tenant users
- Read and Send MS Teams messages and emails
- Navigate Sharepoint sites and OneDrive files and directories
- Register Malicious OAuth Applications to maintain persistence
Example: Device Code Phishing Attack in Action Link to heading
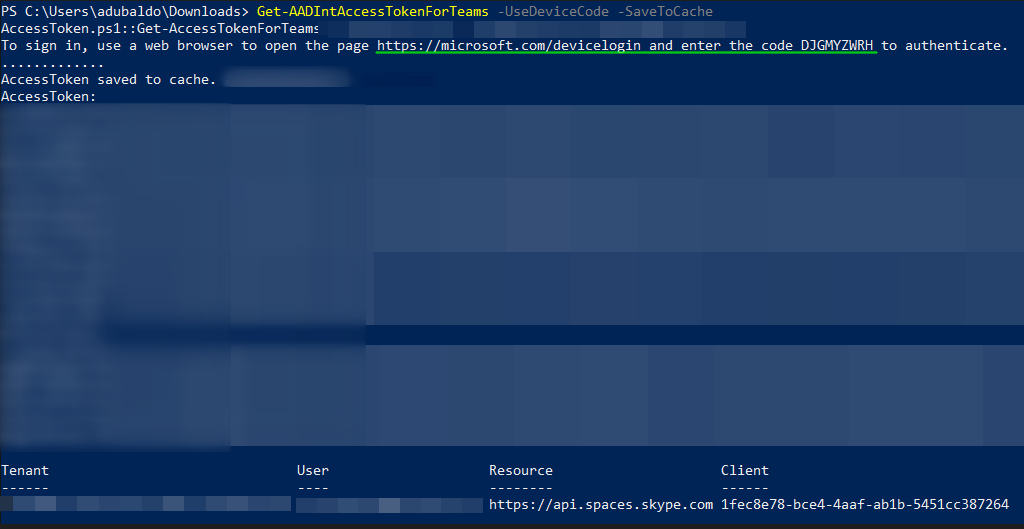
In this example, I used AADInternals to get the Teams access token, then switched to GraphRunner to make some tasks easier.
GraphRunner is a post-exploitation toolset for interacting with the Microsoft Graph API. It provides various tools for performing reconnaissance, persistence, and pillaging of data from a Microsoft Entra ID (Azure AD) account.
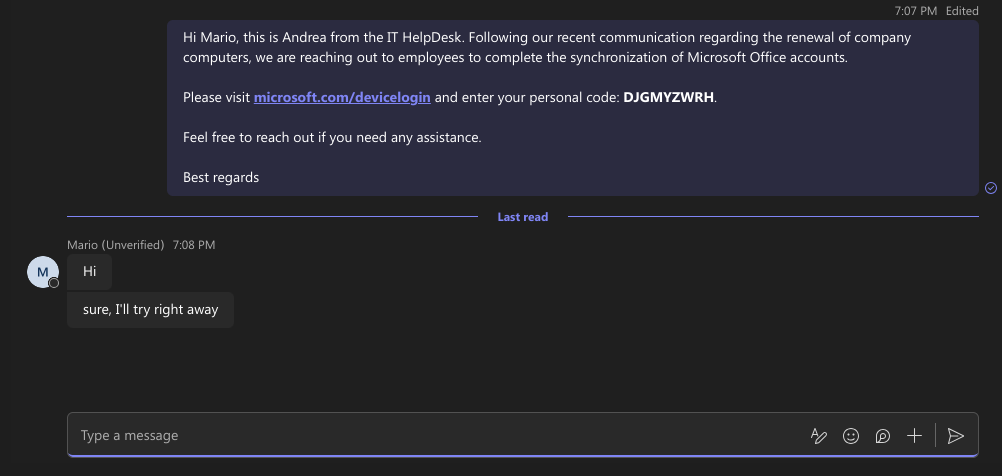
1. Phishing Message on Microsoft Teams Link to heading
The attacker sends a phishing message or vishing via Microsoft Teams , posing as IT support or an automated system, instructing the victim to authenticate a device using a code. The message contains a seemingly urgent request:
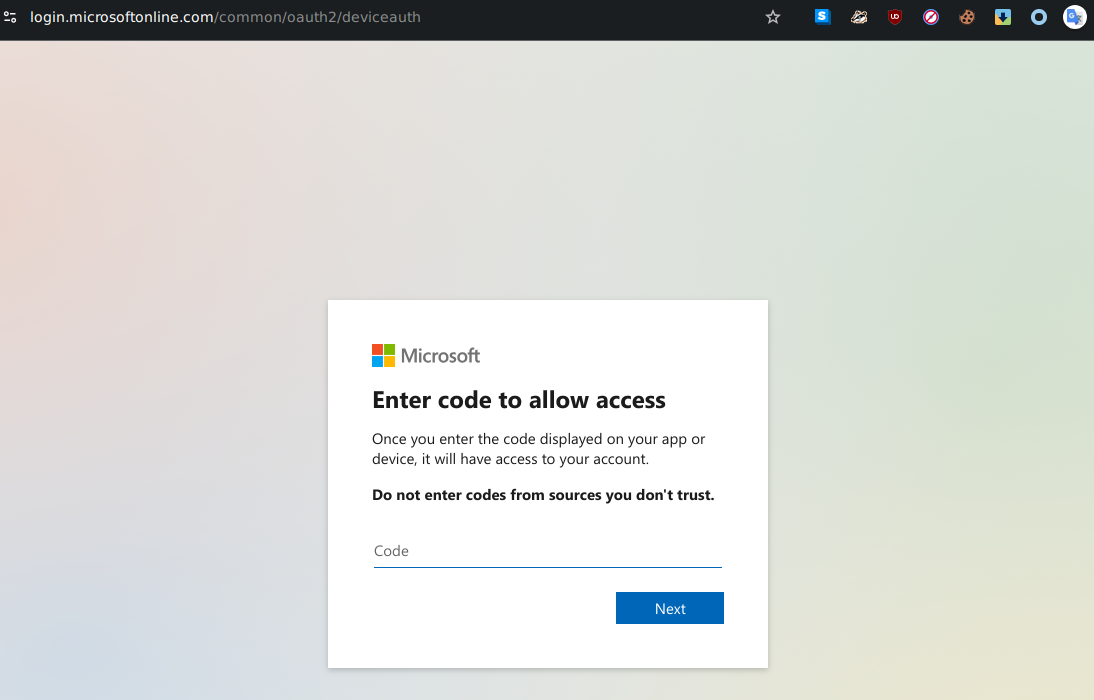
2. Victim Accesses Microsoft Login Page Link to heading
The victim, believing the message is legitimate, navigates to the official Microsoft login page and enters the provided device code.
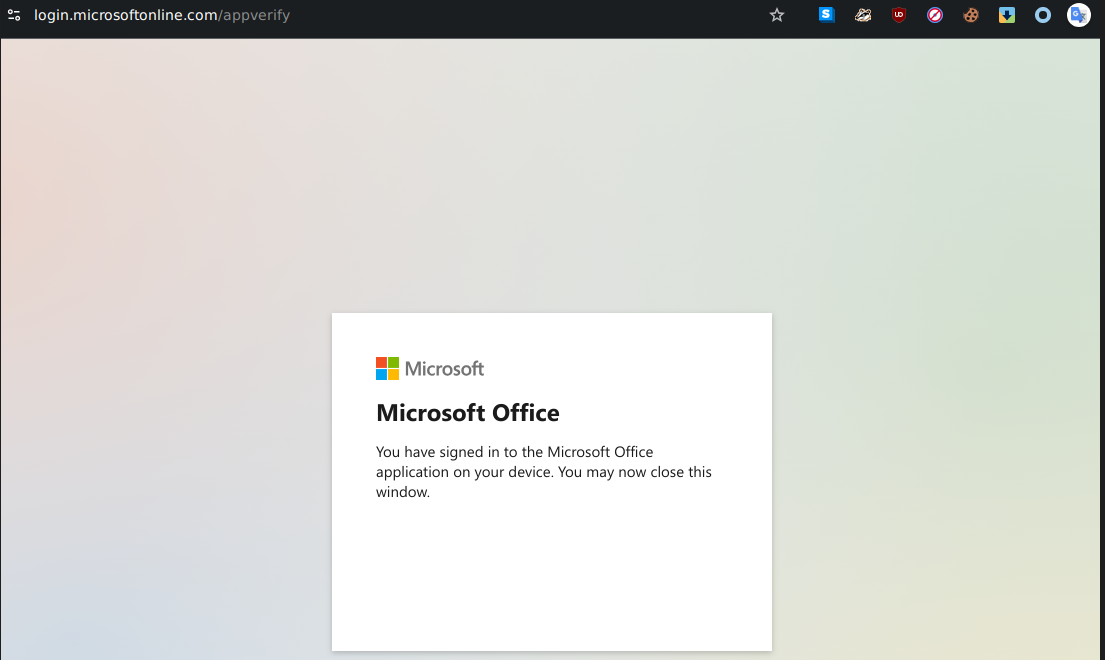
3. Attacker Receives Access Tokens Link to heading
Once authentication is complete, Microsoft issues an OAuth access token and refresh token. The attacker retrieves these tokens via continuous polling and uses them to interact with Microsoft Graph API, accessing emails, sending phishing messages, and exfiltrating data.
In this example I used the Client ID 1fec8e78-bce4-4aaf-ab1b-5451cc387264 which is Client ID for Microsoft Teams on mobile and client. Check the list here.
4. Exfiltration Link to heading
Once the attacker obtains the OAuth tokens, they can be easily leveraged within GraphRunner, automating interactions with Microsoft Graph API. By supplying the stolen tokens, an attacker can:
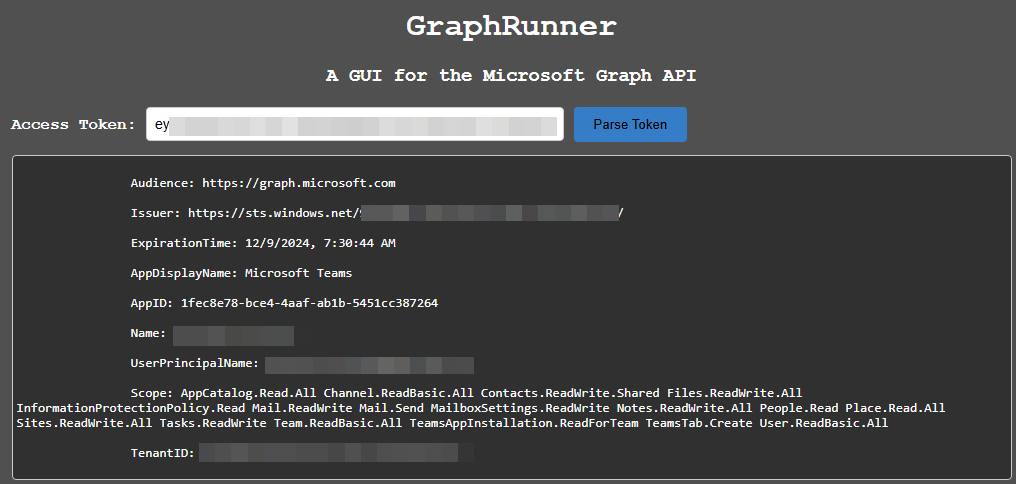
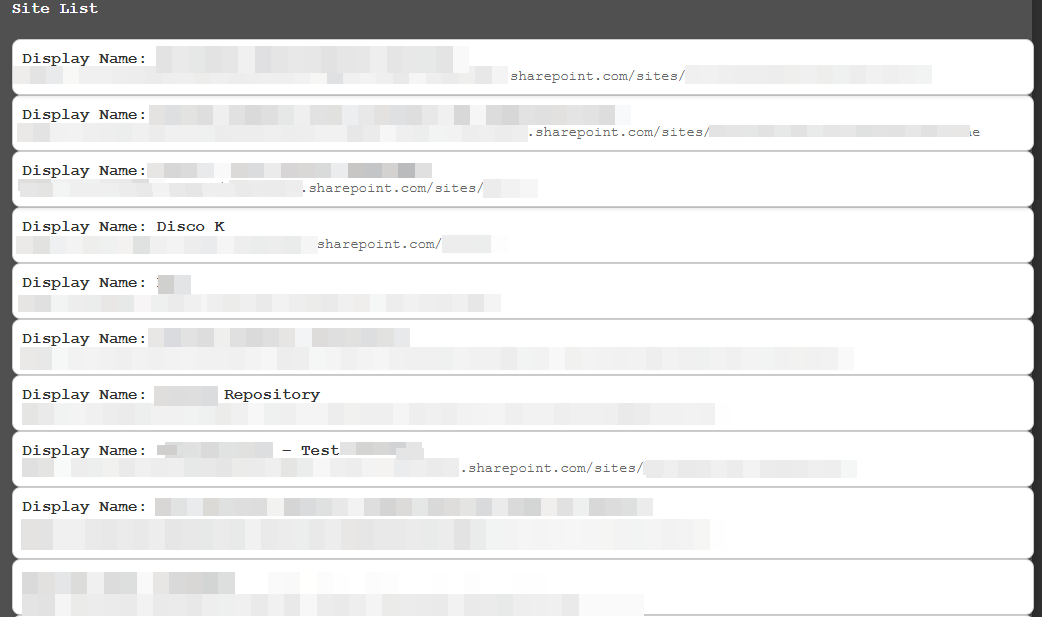
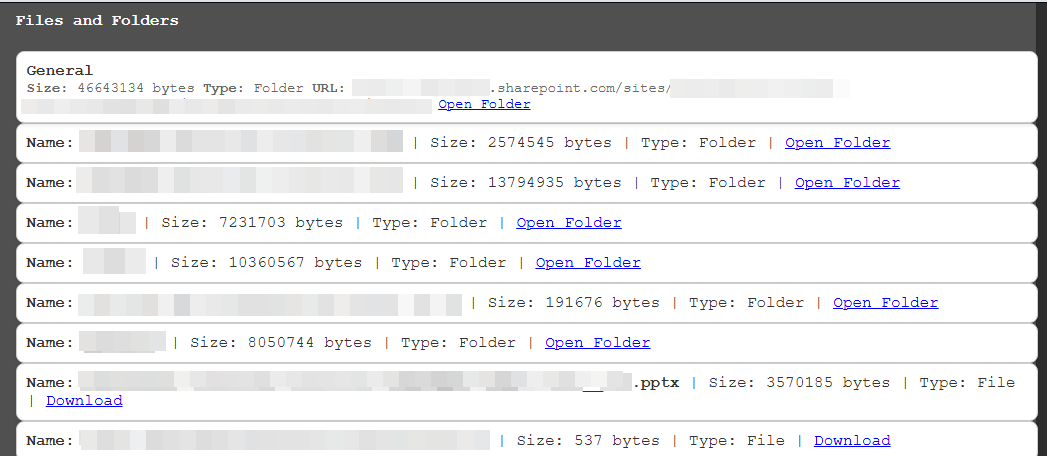
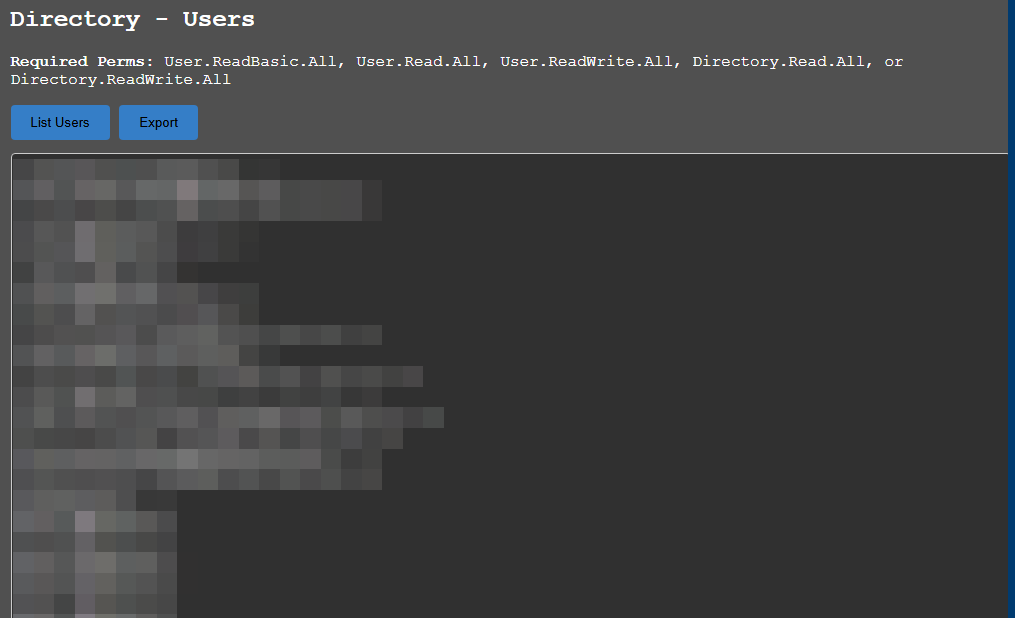
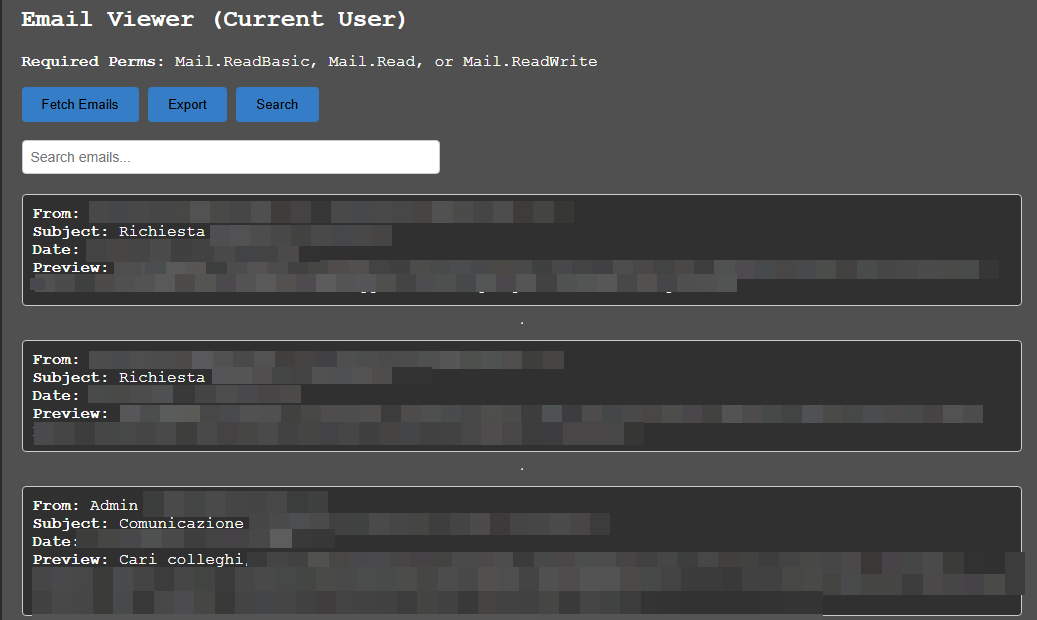

To change the scope and use additional features of Microsoft Graph API, you need to use the refresh token to request a new access token with the desired permissions.
Mitigation by Microsoft Link to heading
Key Defenses Against Device Code Phishing
-
Restrict Device Code Flow: disable device code flow unless absolutely necessary. If required, enforce Microsoft Entra ID Conditional Access policies to regulate its use.
-
User Awareness & Training: educate employees on phishing tactics and ensure they recognize OAuth consent prompts, including verifying application legitimacy before granting access.
-
Revoke Compromised Sessions: if suspicious activity is detected, revoke the user’s refresh tokens using the revokeSignInSessions API and enforce re-authentication.
-
Adopt Best Practices: strengthen security by following Microsoft’s recommended OAuth protection strategies, including continuous monitoring and restricting third-party app permissions.
Full mitigations are listed here.